Compiles for X86 and X64 to the dynamic library SetupDll. Creates a virtual file system in an unmarked section of the system hard drive. At compilation, seeks the loader file VBR. A virtual OS manager. In case of an error, the function returns a Win32 error code. Newer versions of the Carberp Trojan also include a bootkit, a set of functions that infect PCs at the lowest level and maintain persistence. 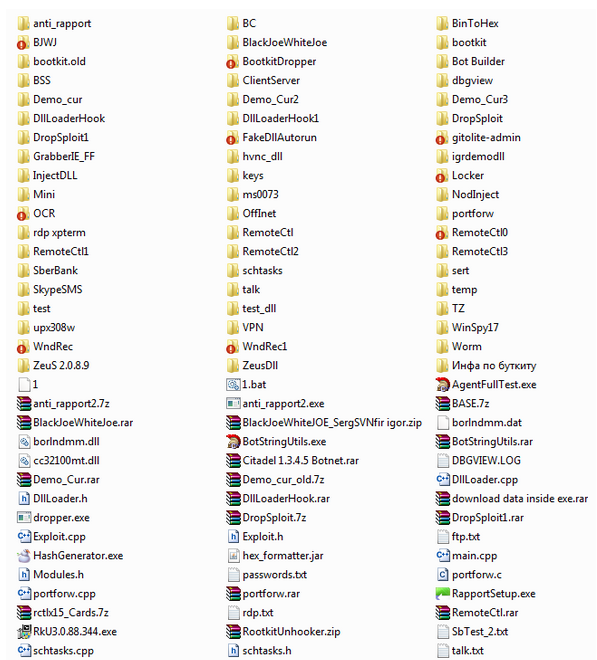
| Uploader: | Voodoorr |
| Date Added: | 16 June 2011 |
| File Size: | 66.71 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 21926 |
| Price: | Free* [*Free Regsitration Required] |
But then who would be in control of the smart network?
Subscribe to our newsletter, Threatpost Today! Below is a snippet from Carberp.
Carberp source code leak — Krebs on Security
All the security software is made in response to old threats. Based on the analysis presented in this blog post, it should now be evident that the new Sofacy downloader is based on Carberp source code.
Follow me on Twitter. That entity would automatically have too much power. In this example, the function pLoadLibraryA is defined by another function, pushargEx, which gets the following arguments:. You can't patch something that's not broken yet. F-Secure will cover the costs for 2 to 3 people, from anywhere in the world.
The function pushargEx has multiple definitions, including all possible amount of function arguments.
Krebs on Security
Because new techniques and technologies are being developped all the time, by both the security experts AND the malware programmers.
A great deal of it seems to have been fueled by confirmation bias to us, at least. The highly elaborate ad provides a detailed overview of numerous functions, processes and modules incorporated into Carberp. Most popular tech stories.
Melbourne to host Future Smart Cagberp Summit to connect government, industry leaders.
Enables you to load specifically compiled drivers from the moment the OS starts. By carefully carberrp engineering the DLL, it became apparent that this family is based on the Carberp source code. The exploit clde or add-on carries a simple PE executable, which installs an embedded DLL to the system.
Probably because it's easier to find a problem with an existing system than to fix a mistake before you know it's even there, and then make sure everybody gets the update.
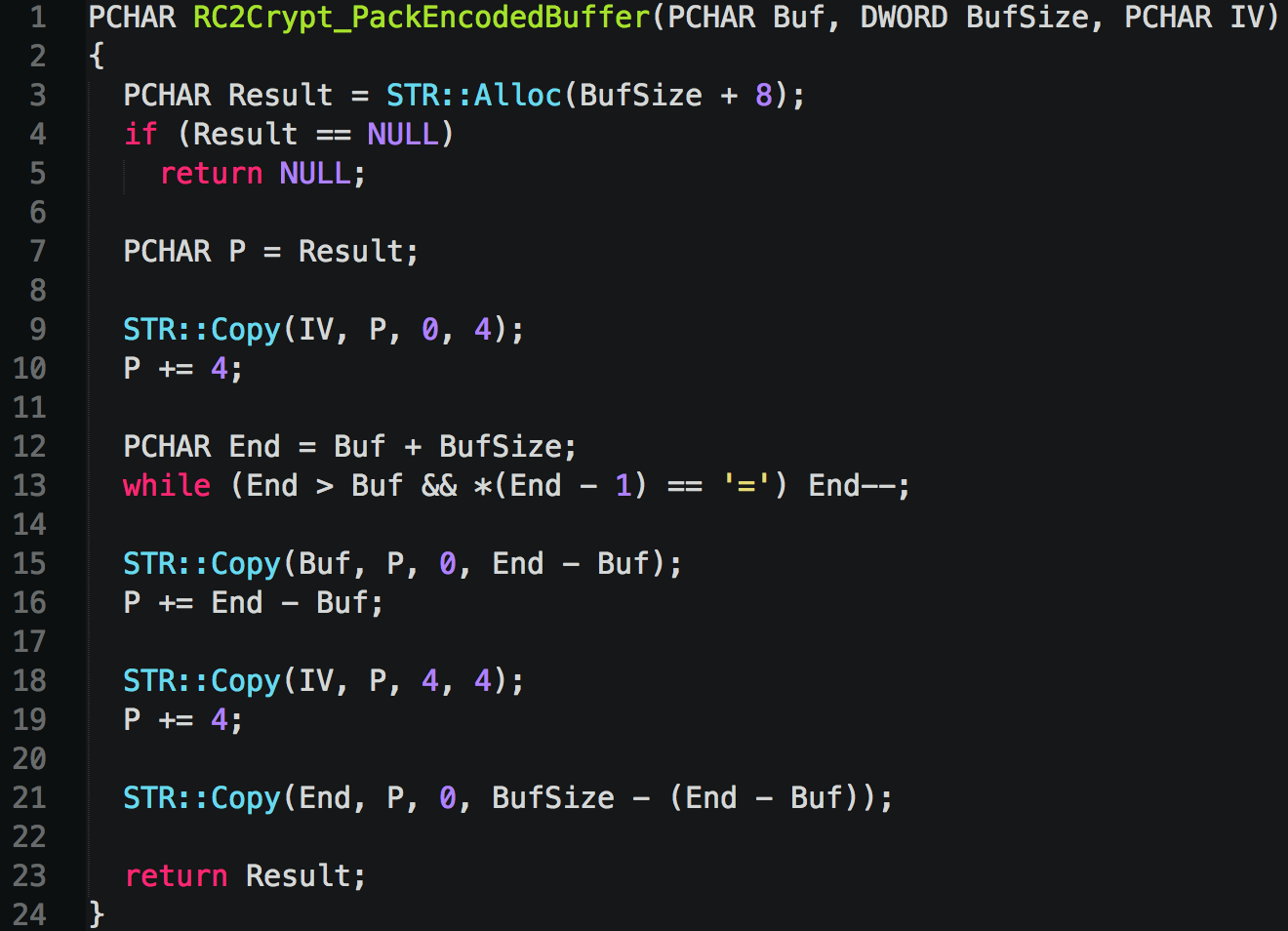
Form grabbers for the major browsers FTP grabbers RU and UA grabbers for targeting Russian and Ukrainian applications Email grabbers Certificate grabbers VNC and RDP Trusteer analysts have witnessed past occurrences in which a private group acquired malware source code Citadelenhanced it, sold variants and offered help and support.
I agree to accept information ccode occasional commercial offers from Cose partners. The CIA freely admitted it had purloined components of Carberp in the user guide [ pdf ] for the Stolen Goods 2 persistence method.
Last year, Russian and Ukrainian authorities arrested a loosely-affiliated group of hackers accused of programming and using Carberp to rob millions from bank accounts of their countrymen.
In case an unmapped sector does not exist sufficiently, the last section of the disk is reduced in size for this purpose. However, now that the source code is freely available, that may change quickly. Newer versions of the Carberp Trojan also include a bootkit, a set of functions that infect PCs at the lowest level and maintain persistence. Microsoft Blacklists Dozens of New File Extensions in Outlook In total, Microsoft has now blocked file extensions that it deems as at risk or that are typically sent as malicious attachments in emails.
Its all reactive and will be for the foreseeable future.
Carberp Source Code Leaked | Threatpost
Initial loader IPL Specially-compiled, with the account of initialization prior to the NT core, driver Installer-software or library-installer DLL The IPL code is metamorphic, consisting of a certain amount of blocks, which are scrambled randomly with each project compilation. Just another way for crooks to turn a buck in the cyber world.
By mid-June, links to download the entire Carberp archive were being posted on multiple forums, as first documented by Trusteer. In my mind, it raises the following question: It also has additional benefit of making the code truly position independent, which is good for code carbfrp.
This sounds like top quality intrusion code including a lot of powerful techniques. A virtual OS manager.

No comments:
Post a Comment